Ransomware: What is CryptoLocker and how can you avoid it?
Ransomware continues to pose a major threat to today’s internet users. A recent report from Sophos found 59% of respondents reported being affected, a figure certain to rise as cybercriminals become increasingly experienced at targeting innocent users.
CryptoLocker is a fairly new family of ransomware which first hit our computer files back in 2013 and it is still making life hell for those unlucky enough to be infected with it.
CryptoLocker is a ransomware trojan which targets computers running Microsoft Windows, based on extorting money from users. CryptoLocker hijacks users’ documents and asks them to pay a ransom, through either bitcoin or a pre-paid cash voucher, with a time limit to send the payment. If the deadline is not met, the malware offers to decrypt data via an online service provided by the malware’s operators, for a significantly higher price in bitcoin.
Some victims claim that paying the ransom does not always lead to the files being decrypted.
Numerous variations of the virus have since popped up which can exploit programs like Adobe Flash and Internet Explorer. Some of these are Cryptowall, TorrentLocker, CTB-Locker and TeslaCrypt. Read more about these variants here. TeslaCrypt has the most number of infections seen widely across all countries and gives the option to use Bitcoin, PaySafeCard or Ukash for payment.
How do you become infected with ransomware?
You can become infected with ransomware in a few different ways.
CryptoLocker takes advantage of Windows’ default behaviour of hiding the extension from file names to disguise the real .EXE extension. It is typically propagated as a ZIP file attachment to an email message, which contains an executable file with the filename and the icon disguised as a PDF file.
As soon as the victim runs it, the Trojan goes memory resident on the computer and takes the following actions:
- Saves itself to a folder in the user’s profile (AppData, LocalAppData).
- Adds a key to the registry to make sure it runs every time the computer starts up.
- Spawns two processes of itself: One is the main process, whereas the other aims to protect the main process against termination.
TeslaCrypt is distributed widely via the Angler exploit kit and a few other known exploit kits. Using Angler, it exploits Adobe Flash and, once successfully exploited, it downloads TeslaCrypt as a payload.
How do I know I have ransomware on my computer?
Users will receive a message popup that may look something like this:
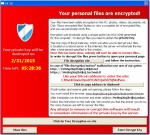
How to avoid CryptoLocker and other ransomware
Sophos and ITRiver recommend using the following guidelines to keep your systems safe from ransomware:
- Regular backup: Although ransomware itself can be removed from your computer or device, files remain encrypted in a way which researchers consider unfeasible to break, so it is ESSENTIAL for all businesses to regularly backup their files. This will help mitigate the damage caused not only by malware infections, but hardware problems or any other incidents as well. We also strongly recommend you keep an offline version of your backups to ensure they don’t become encrypted as well.
- Up to date antivirus: Using a premium up-to-date antivirus such as Sophos HIPS technology is also highly recommended to block ransomware proactively.
- Apply windows and other software updates regularly: Keep your system and applications up to date. This gives you the best chance to avoid your system being exploited using drive-by download attacks and software (particularly Adobe Flash, Microsoft Silverlight, Web Browser, etc.) vulnerabilities which are known for installing ransomware.
- Be email smart: Be particularly wary of emails from senders you don’t know, especially those with attached files. Most ransomware arrives via spam email either by clicking the links or as attachments. Having a good email anti-virus scanner would also proactively block compromised or malicious website links or binary attachments that lead to ransomware.
- Disable hidden file extensions in Windows to make it easier to recognise this type of attack.
- Install a firewall, block Tor and I2P, and restrict to specific ports: This prevents the malware from reaching its call-home server via the network, and can disarm an active ransomware variant. As such, blocking connections to I2P or Tor servers via a firewall is an effective measure.
- Disable remote desktop connections: When they are not required in your environment, it is best to disable remote desktop connections so that malicious authors cannot access your machine remotely.
Retrieving your files after a ransomware attack
As mentioned above, BACKUP YOUR FILES DAILY. It is the only way to ensure you can retrieve your files.
If you become infected and don’t have a backup copy of your files, we recommend that you do NOT pay the ransom, as it turns the malware into a highly profitable business model and will contribute to the flourishing of this type of attack.